Aqua Nautilus researchers recently discovered that attackers can easily impersonate popular Visual Studio Code extensions and trick unwitting developers into downloading them. VSCode is by far the most popular IDE;According to a StackOverflow surveyout, which is currently Used by 74.48% of developers.The power of VSCode lies in its wide variety of extensions,VSCode Marketplace There are over 40,000 extensions in China.
As a VSCode user, it is also a question of whether the VSCode extensions used are trustworthy or legal.According to the introduction, althoughThere are several features that help protect developers from malicious extensions.For example, MicrosoftensureA virus scan is run on every new extension and every extension update. The extension will not be published on the Marketplace for public use until the scan results are correct. As well as steps taken to prevent name squatting, where names are deliberately similar to well-known names.Developers can also observe whether the extension has a blue tick, which means that the publisher has verified the ownership of a web domain name (some genuine extensions have not been verified, such as Prettier et al.).

Popular Extensions in the Marketplace
But researchers point out that even for security-conscious developers, accurately distinguishing malicious from benign extensions can be a challenge. And put forward several arguments:
- Anyone can sign up to be an extension publisher, even using a new disposable email address.
- The extension’s extension name and publisher name do not have to be unique, existing names can be copied.In the example given, the researchers start withTaking the popular VSCode extension Prettier as an example, a new extension in disguise has been created. A closer look at the URL reveals that,The difference is the publisher name (esbenp vs espenp) and the extension (prettier-vscode vs pretier-vscode).When a user correctly searches for the Prettier extension, the mock extension comes up at position 26, and the risk is low. But if a developer inadvertently mistypes “pretier“, the cloaked extension is the only search result.
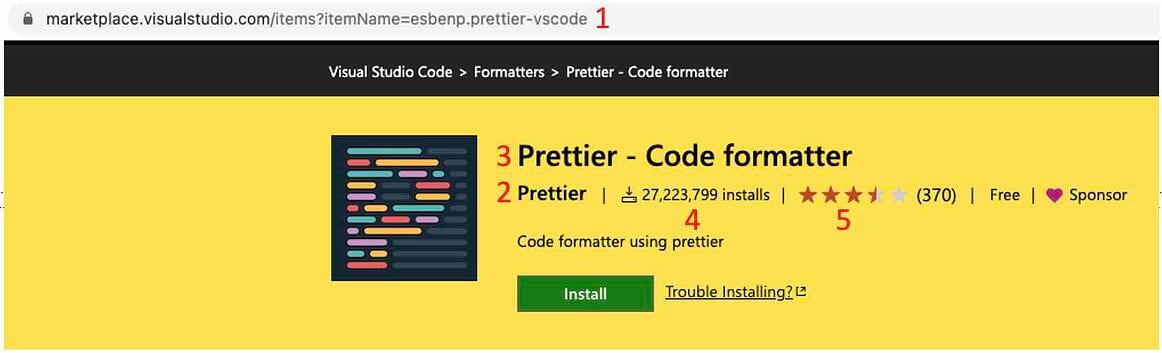
Genuine
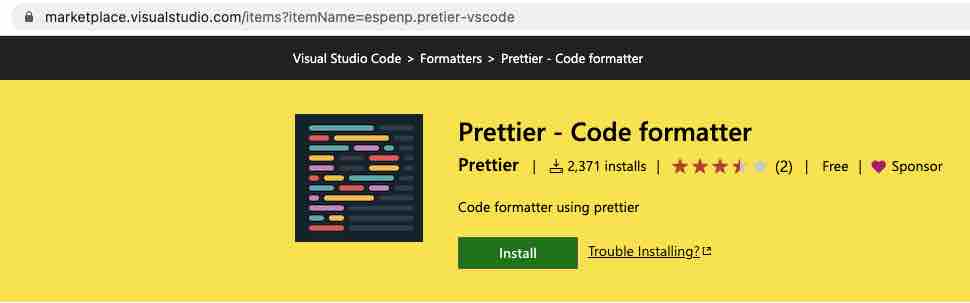
piracy
- A publisher’s blue checkmark only proves ownership of a domain. “Publishers can buy any domain name and register it to get that verified tick.”
- The number of downloads and comments is useful, but these things can be programmed and faked.
The Aqua team failed to demonstrate that the malicious extension would pass Microsoft’s virus checker.However, the data show that the published Prettier masquerade extension,Installed over 1000 times worldwide in less than 48 hours. VS Code extensions run with the same permissions as the user, so if a malicious extension is installed, it is likely to cause damage.
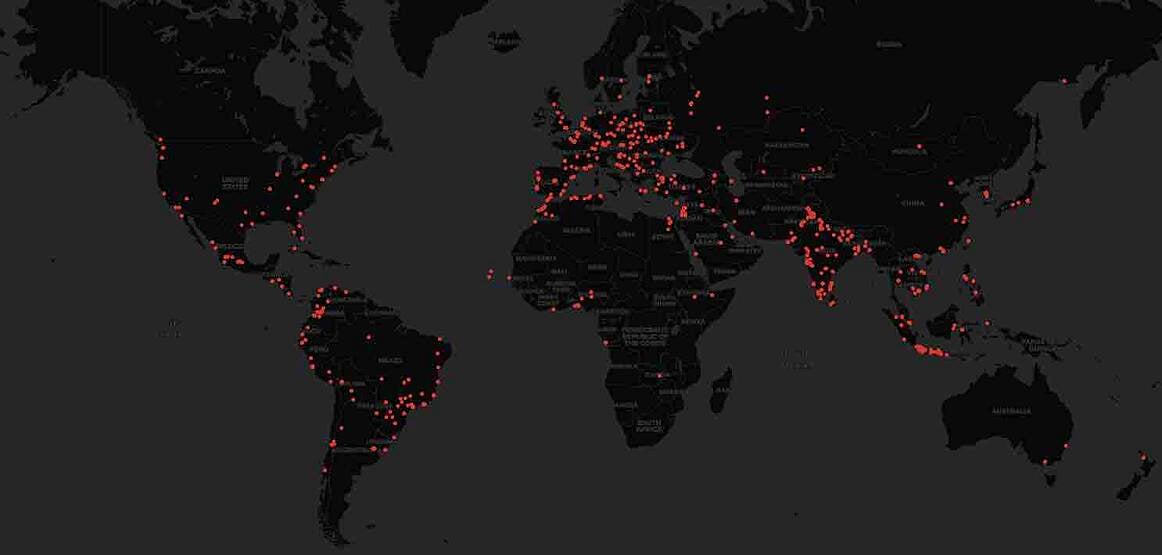
The researchers concluded that the threat of malicious VSCode extensions is real. It may not have received much attention in the past because no major impact events have occurred. However, attackers have been working to expand their arsenal of techniques that allow them to run malicious code within an organization’s network. “As researchers, we are here to uncover such threats and raise community awareness of these new potential entry points.”
It’s also important to note that VSCode extensions are written in Node and packages are downloaded from NPM, so there’s always the threat of malicious code packages being uploaded to package managers like NPM. So there is a real risk that an uninformed legitimate developer could unknowingly use a malicious package from NPM as a dependency of their extension, causing the entire extension to break and unknowingly endangering the community .
In addition to VSCode extensions, the Marketplace also provides extensions for Visual Studio and Azure DevOps; they also have the same risk, but researchers have not yet tracked down relevant clues. “As always, be vigilant about the extensions you install, and remember that each one runs with the user’s privileges.“
See the full report for details.
#Code #extension #trustworthy #News Fast Delivery