
HummerRisk is an open source cloud-native security platform that performs comprehensive security inspections on cloud-native environments in a non-invasive manner. We focus on solving three problems, the underlying hybrid cloud security compliance, the middle-level K8S container cloud security and the upper-level software security.
Architecture diagram
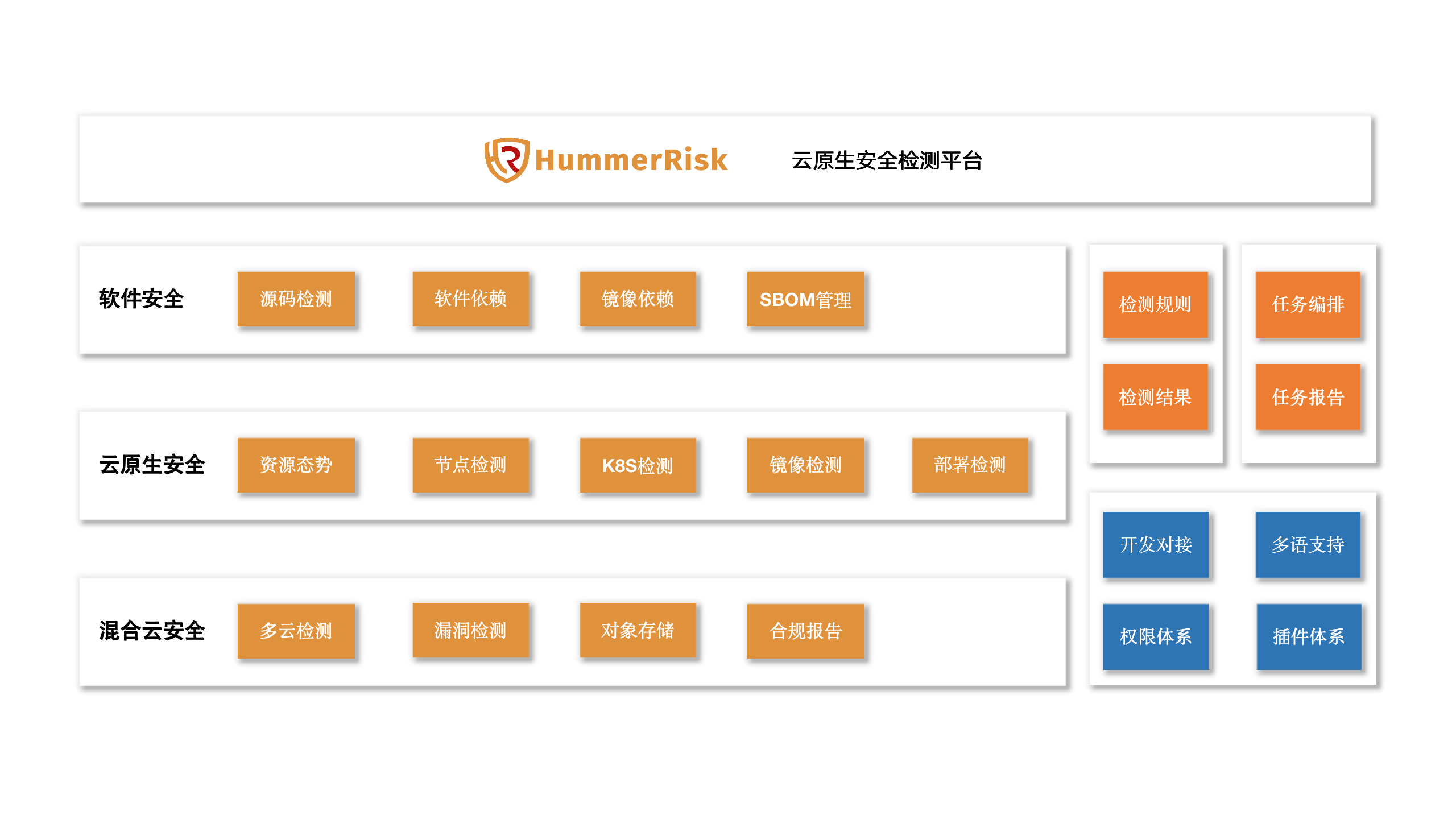
What HummerRisk can do
Hybrid Cloud Security
- Hybrid cloud security compliance detection: Perform security compliance detection on mainstream public (private) cloud resources, such as Qualcomm 2.0 pre-inspection, CIS compliance inspection, various baseline detections, and customizable detection rules;
- Vulnerability detection: Based on the vulnerability rule base, the security vulnerabilities of specified network devices and application services are detected by scanning and other means;
- Compliance Reports: One-click access to compliance reports to gain complete control over your security posture.

What are the advantages? * Comprehensive support: Almost all public clouds supported, including: Alibaba Cloud, Tencent Cloud, Huawei Cloud, Volcano Engine, Baidu Cloud, Qingyun, UCloud, Amazon Web Services, Microsoft Azure, Google Cloud, and supported private clouds include: OpenStack, VMware vSphere, and is constantly expanding the scope of support; * Easy to use: just bind a cloud account, you can perform detection with one click; * Out of the box: a large number of built-in rules, and you can customize the rules as needed.
K8S Container Cloud Security
- K8S resource situation: You can associate multiple K8S clusters to view the resource situation of each associated environment in a unified manner;
- Environmental detection: Detecting according to the K8S security baseline, and discovering the existence of configuration errors, security loopholes, dangerous actions, etc.;
- Mirror detection: Comprehensive detection of mirror-related vulnerabilities, including operating systems, software packages, application dependencies, etc.;
- Container detection: Scan and detect running containers to discover existing security issues and risk content;
- Deployment detection: Detect K8S deployment orchestration files and discover configuration problems before deployment;
- Host detection: You can customize the detection content to find problems in the underlying host/virtual machine.
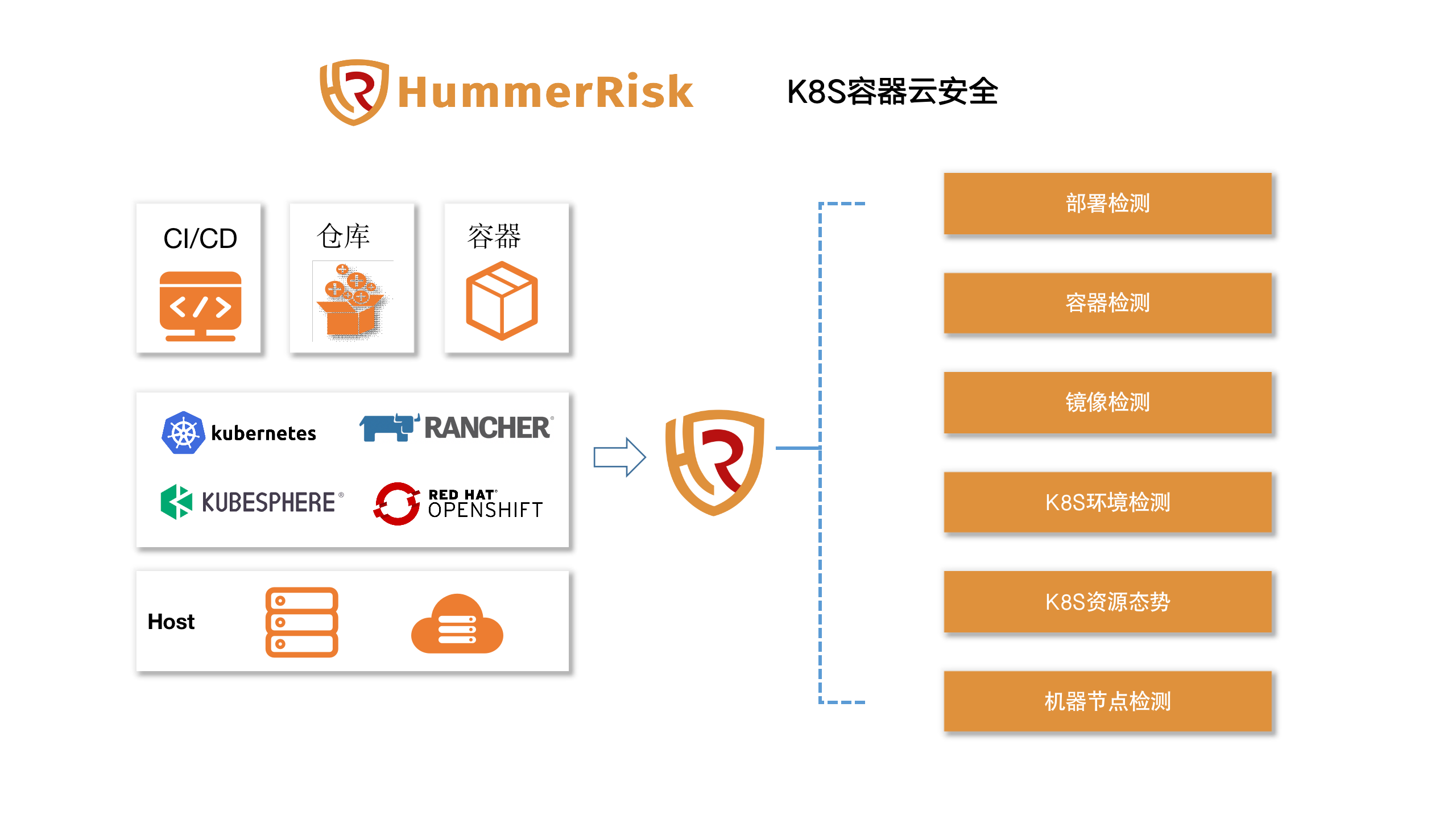
What are the advantages?
* Compatibility: Supports multiple K8S distributions; * Independence: Neutral product, objective detection; * Non-invasive: Non-invasive detection.
software security
Based on the combined detection of source code, software and image, it helps enterprises to build and continuously manage SBOM, and improve the security of software supply chain and open source. * Source code detection: Detect the developer’s source code, and discover open source protocols, dependencies, loopholes, codes and other problems in advance; * Software dependency detection: Through the analysis of software components, find dependency loopholes, and build SBOM at the same time; * Mirror dependency detection : Detect various dependency information in the image and discover security vulnerabilities; * SBOM management: Visual management and analysis of SBOM, detect changes in SBOM, quickly discover and locate risks and vulnerabilities in the software supply chain, and give reasonable handling suggestions .
What are the advantages?
* Full life cycle: Covers multiple stages of development, construction, operation, etc., and supports docking with multiple warehouses; * Automatic processing: The processing and construction process of SBOM is completed automatically; * Visualization: Provides a convenient visual interface for management and analysis.
Technical advantages
- Open source and open: HummerRisk follows the GPL v3 open source license;
- Non-intrusive: based on the non-intrusive implementation, get started quickly and reduce potential risks;
- Comprehensive support: from the underlying basic environment to the upper-level software applications, covering all aspects of the cloud native environment;
- Rich rules: a large number of built-in detection rules, such as CIS rules, etc., and support for custom rules;
- Support Xinchuang: Support deployment in Xinchuang environment.
#HummerRisk #Homepage #Documentation #Downloads #Cloud #Native #Security #Detection #Platform #News Fast Delivery
