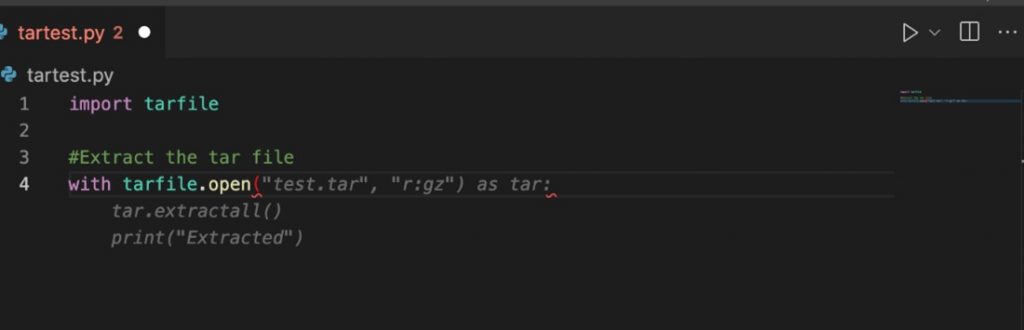
Security company Trellix Kasimir Schulz, a researcher at thepath traversalvulnerability,Allows attackers to gain access to the file system.After further analysis, he discovered that it was a vulnerability in the Python tarfile that had been disclosed as early as 2007 CVE-2007-4559;produced inIn code that uses the unprocessed tarfile.extract() function or the built-in default of tarfile.extractall().
The vulnerability is 15 years old and first reported in August 2007ReportSince then, itsrelatedThe technical details have also been available.But currentlyNo patches have ever been received, and the only mitigation provided is a documentation update that warns developers about the risks.official Python DocumentationA clear warning says “never extract archives from untrusted sources without first checking”.BleepingComputer pointed out,While there are no reports of the vulnerability being used in an attack, it still represents a risk in the software supply chain.
Trellix researchers pointed out that the vulnerability has existed in thousands of open source/closed source projects. They scraped a set of 257 repositories more likely to contain vulnerable code and manually checked 175 of them to see if they were affected. The results showed that 61% of these projects were vulnerable; after an automated check of the remaining repositories, the number of affected projects increased to 65%, indicating the prevalence of the problem.
However,This small sample set serves only as a baseline for estimating all affected repositories on GitHub. “With the help of GitHub, we were able to obtain a larger dataset of 588,840 unique repositories that contained ‘import tarfile’ in their Python code”.
based onWith a manually verified vulnerability rate of 61%, Trellix estimates there are more than 350,000 vulnerable repositories, many of which are used by machine learning tools like GitHub Copilot that help developers be more productive. This automated tool relies on code from hundreds of thousands of repositories to provide “auto-complete” options. If they provide unsafe code, the problem can spread to other projects without the developer’s knowledge.
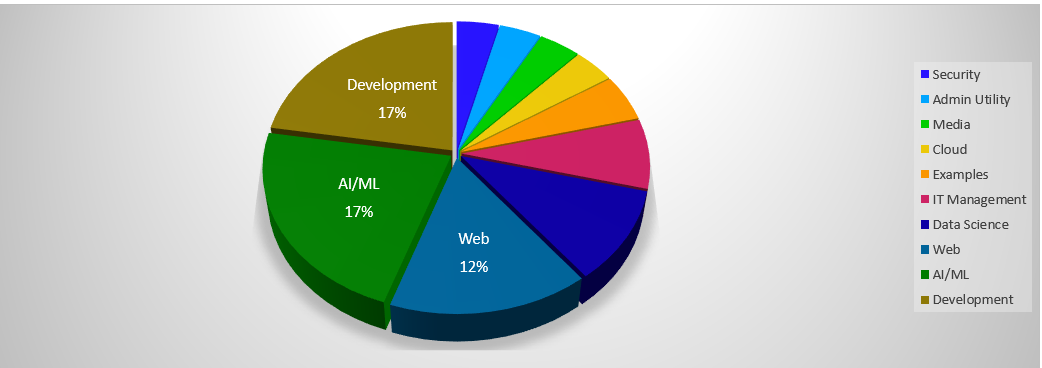
Open source code vulnerable to CVE-2007-4559 “spans across industries.”inthe development sector is most affected, followed by networking and machine learning technologies.
Trellix aspect is 11,005 repositories provide patches:Available in branches of affected repositories and can be added to the main project via pull requests.Due to the high number of affected repositories, researchersThis patching is expected to continue over the next few weeks. “This is expected to affect 12.06% of all vulnerable projects, and over 70,000 projects by the time of completion. This is a large number, but by no means 100%, as all Pull Requests must be checked by project maintainers accept”.
BleepingComputer has reached out to the Python Software Foundation for comment on CVE-2007-4559, but has not received a response at the time of publication.
See the full report for more details.
#Years #Unpatched #Python #Vulnerability #Affects #Projects #News Fast Delivery