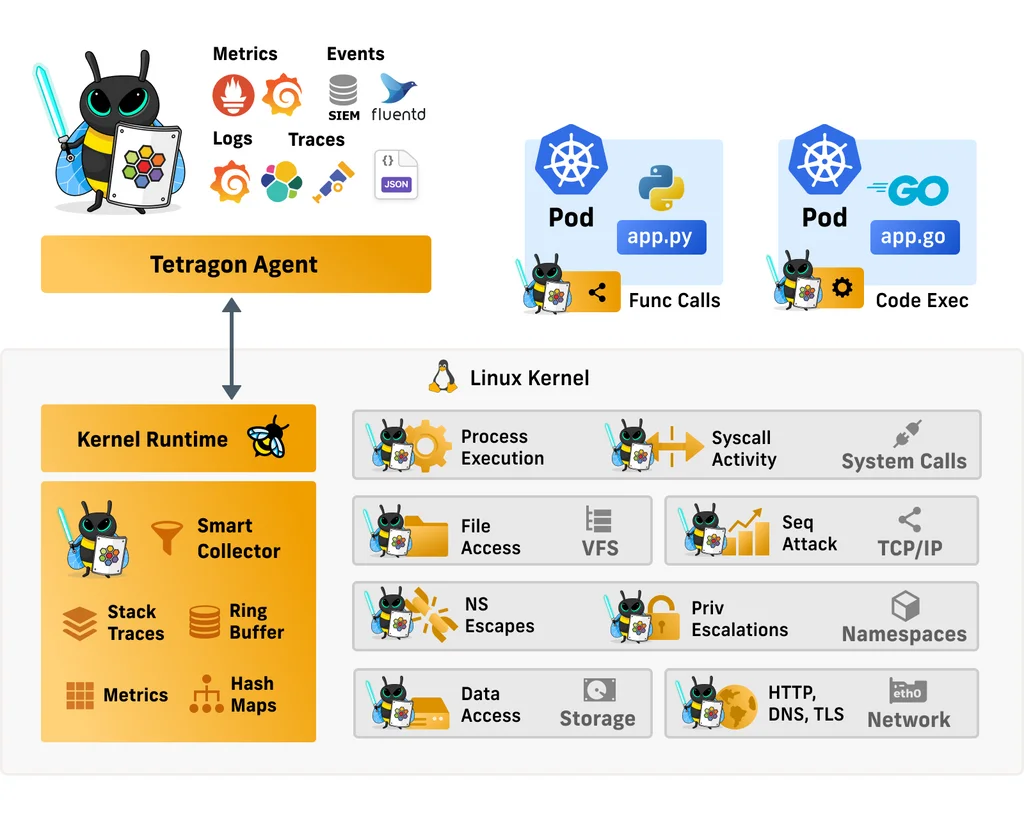
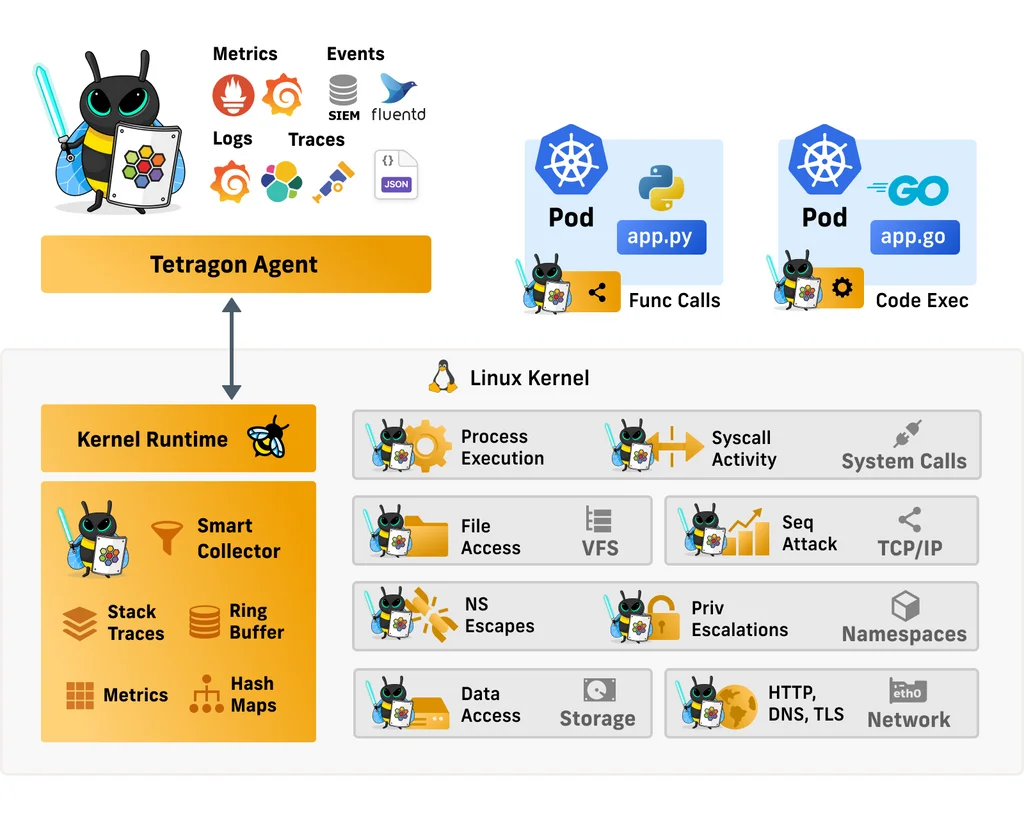
Tetragon is an open source eBPF-based security observability and runtime enhancement component from Cilium.
Tetragon is able to detect and react to important security events such as
- Process execution event
- system call activity
- I/O activity, including network and file access
When used in a Kubernetes environment, Tetragon is Kubernetes-aware — that is, it understands Kubernetes identities such as namespaces, Pods, etc. — so security event detection can be configured for individual workloads.
Functional Overview
eBPF real-time
Tetragon is a runtime security implementation and observability tool. This means that Tetragon applies policies and filtering directly in the kernel’s eBPF. It performs filtering, blocking, and reacting to events directly in the kernel, rather than sending events to a userspace agent.
For observability use cases, applying the filter directly in the kernel greatly reduces the observation overhead. eBPF reduces the required resources by avoiding expensive context switches and wakeups, especially for high-frequency events such as send, read, or write operations.
Instead, Tetragon provides rich filters (files, sockets, binary names, namespaces/functions, etc.) in eBPF that allow users to specify important and relevant events in their specific context and pass only those events to User space agent.
eBPF flexibility
Tetragon can connect to any function in the Linux kernel and filter its arguments, return values, relevant metadata collected by Tetragon about the process (for example, executable name), files, and other attributes. By writing tracing policies, users can address various security and observability use cases.
Tetragon allows for hooking deep into the kernel, where userspace applications cannot manipulate data structures, avoiding the common problems of system call tracing where data is read incorrectly, changed maliciously by an attacker, or due to page faults and other user/kernel boundary errors lost.Many Tetragon developers are also kernel developers. By leveraging this knowledge base, Tetragon has created a set of tracing policies that address many common observability and security use cases.
eBPF Kernel Awareness
Tetragon provides access to the Linux kernel state through eBPF. Tetragon can then combine this kernel state with Kubernetes awareness or user policies to create rules that are enforced by the kernel in real-time.This allows to annotate and enforce process namespaces and capabilities, process’ sockets, process file descriptors to filenames, and more.
For example, we can create a policy to trigger an alert when an application changes its permissions, or even kill the process before it has a chance to complete a system call and possibly run other system calls.
Development Guide
To get started with local development, refer to the development guide.
#Tetragon #Homepage #Documentation #Downloads #eBPFbased #Security #Observability #Runtime #Enhancements #News Fast Delivery
Tetragon Homepage, Documentation and Downloads – eBPF-based Security Observability & Runtime Enhancements – News Fast Delivery